Security audit
Our approach
For a classic audit mission of overall security, our approach focuses on the following steps:
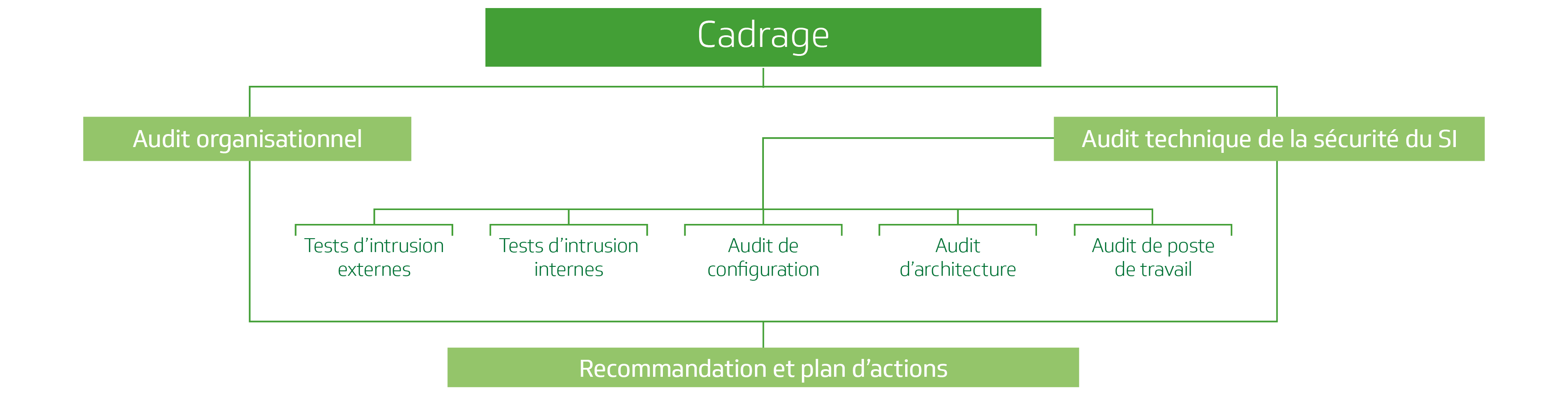
Organizational audit
Organizational audits are carried out in accordance with the ISO 27001 standard, hence covering all the chapters of the standard such as:
- Information security policies
- Organization of information security
- Security related to human resources
- Asset management
- Access control
- Cryptography
- Physical and environmental security
- Security related to operations
- Security of communications
- Acquisition, development and maintenance of information systems
- Relationships with suppliers
- Incident management linked to information security
- Information security aspects in business continuity management
- Compliance
Technical audit
The technical audit covers several aspects:
- Blind penetration testing
This consists of carrying out simulations without prior external information. To do so, we put ourselves in the shoes of a hacker who has no knowledge whatsoever of the target company’s IS aside from its name and we attempt to go as far as possible.
- Internal penetration testing
With internal testing, we will have to simulate attacks coming from within, to determine to what extent a user, who has legitimate access to the system, can go. Several scenarios can be explored with these tests. These namely consist of:
- Misuse of authentication mechanisms on business applications
- Sealing audit on critical applications
- Eavesdropping
- Message interception
- Identity theft
- Denial of access
- Earning of privileges
- Architecture audit
With the architecture audit, the DATAPROTECT team shall examine the positioning of different security systems in terms of architecture as well as the security strategy in place for internal and external perimeters. As a result of the analysis, a network security architecture design will be submitted, taking into account the security flaws that were identified, the network sizing as well as new threats that the target organization will have to confront.
- Configuration audit
This consists of reviewing the configurations of security systems and examining them according to industry best practices.
- Workstation audit
This consists of auditing the security of workstations according to industry best practices.
Actions plan
Organizational and technical security audits will allow the DATAPROTECT team to elaborate a detailed action plan and to identify security work streams in the short, medium and long term.
Our assets
Carrying out IS security audit missions was designed as a value-added offering through:
- The carrying out of the mission by expert consultants:
- Trained consultants that are certified in: CEH, OSCP, CISSP, CISA, PCI QSA, PA QSA, CISSP, ISO 27001 Lead Auditor, ISO 27001 Lead Implementer,
- Qualified consultants: demonstrated experience in similar projects
- Due regard to confidentiality: Elaboration of a communication protocol for an increased protection and communication of the audit findings
- An outstanding experience in information system security:
- More than 100 IS security audit missions
- An ongoing monitoring of IS security
- Expertise and specific tools for penetration testing
- Set up of an Ethical Hacking Lab:
- The standard is largely redundant and requires a specific reading
- The 27001 approach is not a guarantee of suitable quality but rather of continuous improvement
- The 27001 approach contributes to regulatory requirements (e.g. PCI-DSS) subject to adjustments of the approach
 French
French English
English

































